Data security
 Data security is an indispensable component of Research Data Management (RDM), especially in an era where vast amounts of sensitive data are generated, shared, and stored digitally. As research becomes increasingly data-intensive and collaborative, ensuring the security and confidentiality of research data is essential to uphold ethical standards, maintain public trust, and comply with legal obligations.
Data security is an indispensable component of Research Data Management (RDM), especially in an era where vast amounts of sensitive data are generated, shared, and stored digitally. As research becomes increasingly data-intensive and collaborative, ensuring the security and confidentiality of research data is essential to uphold ethical standards, maintain public trust, and comply with legal obligations.
Data security in RDM encompasses the strategies, methods, and technologies used to protect data from unauthorized access, corruption, theft, and loss. Implementing robust security measures - such as encryption, access controls, secure storage solutions, and regular security assessments - ensures that the data collected and analysed remains accurate, reliable, and secure throughout its lifecycle.
The need for robust data security in research is driven by several key factors:
- protection of intellectual property: safeguarding proprietary information and research findings from unauthorized access or theft is crucial for maintaining competitive advantage and fostering innovation;
- ethical considerations: researchers have an ethical obligation to protect the privacy and confidentiality of participants, especially when handling sensitive or personal data;
- regulatory compliance: adherence to data protection laws and regulations (e.g., GDPR, HIPAA) is mandatory to avoid legal penalties and reputational damage;
- prevention of data breaches: data breaches can result in significant financial losses, legal consequences, and erosion of public trust in the research institution.
In this chapter, you can expect to learn about:
- the importance of data security in research: understanding why data security is essential for maintaining data integrity, ethical standards, and compliance with regulations;
- common challenges in securing research data: identifying the obstacles researchers and institutions face, such as resource limitations, complex data environments, and evolving cyber threats;
- key security measures in research data management: exploring effective strategies and technologies – like encryption, access control, and regular backups – to safeguard data;
- implementing data security policies in research: learning how to develop and enforce data security policies, including training programs and collaboration with IT and cybersecurity experts;
- regulatory compliance and future trends in research data security: staying informed about data protection laws and emerging technologies that will shape the future of data security in research;
By prioritizing data security, researchers and institutions can protect sensitive information, maintain public trust, and support the advancement of science in an ethical and responsible manner. This commitment not only upholds ethical standards but also enhances the credibility and reliability of scientific findings in an increasingly interconnected world.
Data security in research is critical for maintaining data integrity, confidentiality, and compliance with ethical and legal standards. Breaches in data security can compromise research integrity, harm participants’ privacy, and damage the reputation of both researchers and their institution. Given that research data often contains sensitive information – such as medical records, financial details, personal identifiers, or proprietary business information – data breaches could lead to serious consequences.
Key reasons why Data Security is essential in research:
- protection of sensitive information: in fields like healthcare, social sciences, and engineering, research data may include sensitive details that require stringent protection;
- compliance with regulations: many research projects are subject to data protection laws, such as General Data Protection Regulation (GDPR) in the EU or Health Insurance Portability and Accountability Act (HIPAA) in the USA. These regulations mandate secure data handling practices and impose penalties for non-compliance;
- preservation of data integrity: maintaining data integrity is crucial for the validity and reliability of research findings. Security measures help prevent unauthorized modifications of data, ensuring that the results are based on accurate and untainted information;
- prevention of data breaches: data breaches can lead to financial, reputational, and legal repercussions, and reputational damage for both individual researchers and their institutions. Implementing robust security protocols mitigates these risks;
- trust in the research process: protecting data helps maintain public trust in research community. When participants are confident that their information is secure, they are more likely to engage in studies, enhancing the quality and scope of research;
- ethical responsibility: researchers have an ethical obligation to protect the privacy and confidentiality of their participants. Upholding high standards of data security reflects a commitment to ethical research practices.
By prioritizing data security, research institutions safeguard the ethical and legal aspects of data handling, thereby fostering a responsible and transparent research environment.
Despite the clear need for data security, researchers and institutions face numerous challenges when implementing secure data practices:
- resource limitations: smaller institutions or research groups may lack the budget to invest in high-quality security infrastructure, tools, and comprehensive training programs. Limited financial resources can hinder the adoption of state-of-the-art security measures, leaving data vulnerable to breaches;
- complex data environments: research data often exists in multiple formats and is stored across various platforms and locations, including local servers, cloud services, and personal devices. This fragmentation makes it difficult to apply uniform security measures across all datasets, increasing the risk of security gaps and inconsistencies;
- balancing accessibility with security: researchers require easy and timely access to data for analysis, collaboration and sharing. However, implementing stringent security protocols can impede accessibility, creating a tension between the need for security and the need for efficient research workflows. Finding the right balance is challenging but essential to protect data without hindering research progress;
- human error: a significant number of data breaches result from human error, such as using weak or default passwords, falling victim to phishing attacks, accidental data sharing with unauthorized individuals, or improper data handling practices. Ensuring that all team members adhere to security protocols is difficult, especially in large or dispersed teams;
- rapidly evolving cyber threats: cyber threats are constantly evolving, with attackers developing new methods to exploit vulnerabilities. Institutions must continuously update their security practices and technologies to keep pace with emerging threats. Staying ahead of cybercriminals requires ongoing investment in security infrastructure and expertise, which can be challenging to sustain;
- compliance with multiple regulations: for research projects involving international collaborations or multi-institutional partnerships, researchers may need to comply with varying data protection laws across regions, complicating data security efforts. Navigating these varying legal requirements can be complicated and time-consuming, potentially leading to compliance gaps;
- lack of standardized policies and procedures: in some institutions, there may be a lack of clear, standardized policies and procedures for data security. Without well-defined guidelines, researchers may be uncertain about the best practices to follow, leading to inconsistent or inadequate security measures;
- technological limitations: some research projects rely on legacy systems or specialized equipment that are incompatible with modern security solutions. Updating or replacing such systems can be costly and disruptive, yet failure to do so may expose data to significant security risks.
Addressing these challenges requires a comprehensive approach, combining technological solutions with staff training, policy development, and ongoing monitoring.
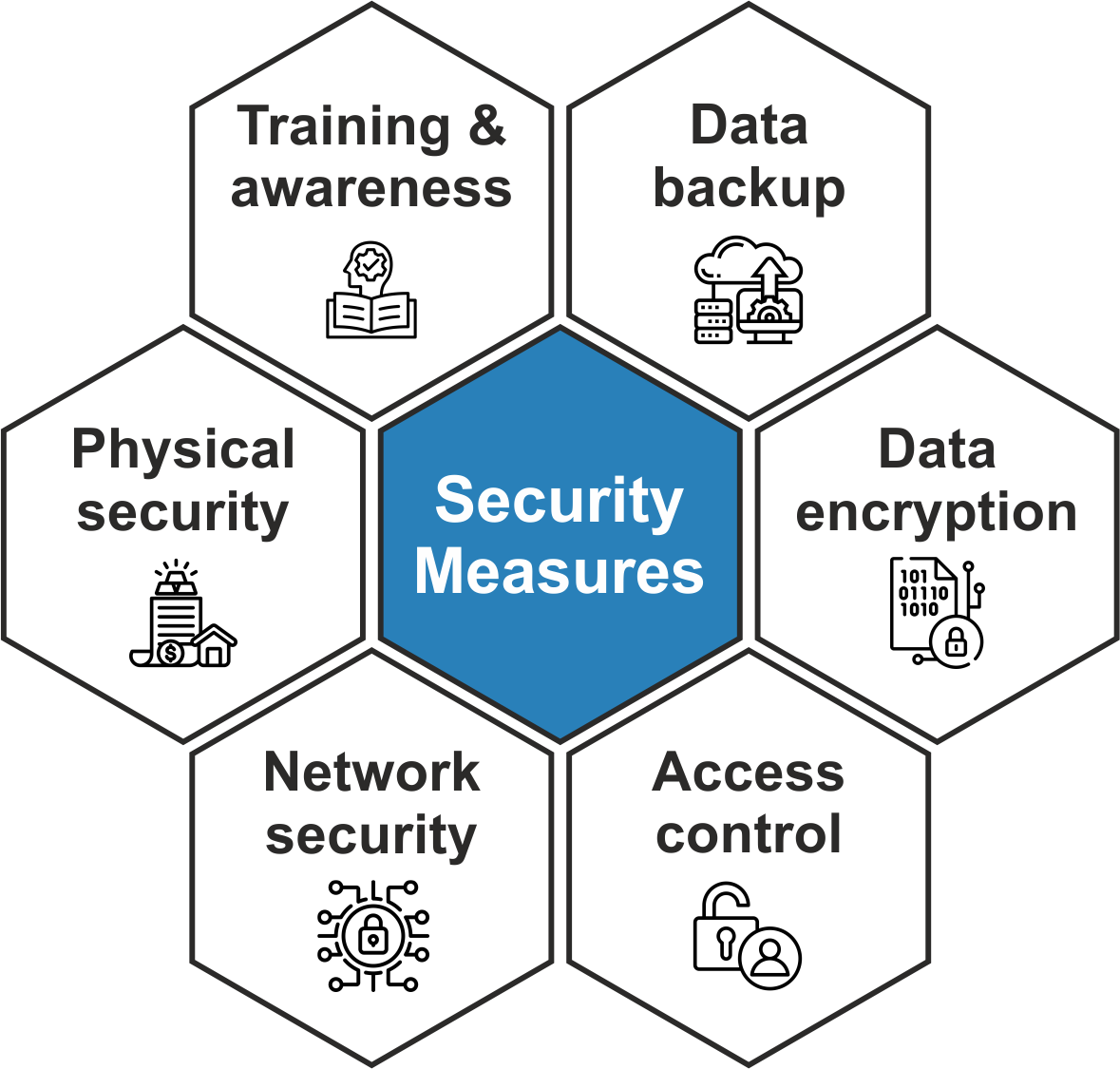
To effectively protect research data, institutions and researchers implement several key security measures. These measures aim to safeguard data from unauthorized access, modification, and loss, ensuring the integrity, confidentiality, and availability of the data throughout its lifecycle.
Essential security measures:
- data encryption: encrypting data both at rest (when stored) and in transit (when being transmitted) is crucial. Encryption transforms data into an unreadable format for unauthorized users, ensuring that even if data is intercepted or accessed without permission, it remains indecipherable. Utilizing strong encryption algorithms and managing encryption keys securely are vital components of this process;
- access control and authentication: implementing strict access controls ensures that only authorized personnel can access specific data files. This involves:
- Role-Based Access Control (RBAC): assigning permissions based on user roles within the organization, limiting access to data necessary for their responsibilities;
- Multi-Factor Authentication (MFA): requiring users to provide multiple forms of verification (e.g., password, security token, biometric verification) adds an additional layer of security against unauthorized access;
- data anonymization and de-identification: for datasets containing sensitive or personal information, anonymizing or de-identifying data protects participant privacy. Techniques include:
- removing personal identifiers: eliminating direct identifiers like names, addresses, and Social Security numbers;
- data masking and obfuscation: modifying data to prevent the identification of individuals while retaining the utility of the dataset for research purposes;
- using pseudonyms: replacing identifiers with pseudonyms or codes that cannot be traced back without a secure key;
- regular backups and disaster recovery: implementing regular data backups and a well-defined disaster recovery plan protect against data loss due to cyber-attacks, hardware failures, or natural disasters. A comprehensive disaster recovery plan includes:
- backup frequency and methods: Determining how often backups are performed and where they are stored (e.g., off-site, cloud storage);
- recovery procedures: establishing clear steps for data restoration and system recovery to minimize downtime;
- testing the plan: regularly testing the disaster recovery plan to ensure its effectiveness;
- network security: protecting data from unauthorized access over networks involves:
- firewalls: implementing network firewalls to monitor and control incoming and outgoing network traffic based on predetermined security rules;
- intrusion detection and prevention systems (IDPS): utilizing systems that detect and prevent malicious activities or policy violations;
- secure connections: Using Virtual Private Networks (VPNs) and secure communication protocols (e.g., HTTPS, SSL/TLS) to protect data during transmission;
- logging and monitoring: keeping detailed logs of data access and modifications helps detect suspicious activities and enables quick response to potential security breaches;
- security training and awareness: educating researchers and staff on data security best practices reduces the risk of human error:
- regular training sessions: providing ongoing education on topics like phishing awareness, password management, and secure data handling;
- clear policies and procedures: establishing and communicating clear guidelines for data security responsibilities;
- physical security controls: protecting physical access to servers and data storage devices through:
- secure facilities: using access controls like key cards, biometric scanners, and surveillance systems;
- equipment security: ensuring that laptops, external drives, and other devices containing sensitive data are secured against theft or unauthorized use.
These measures are essential for establishing a strong data security framework, protecting research data from various threats while ensuring compliance with ethical standards.
Implementing effective data security policies in research environments involves both technical strategies and clear guidelines for data handling. Institutions and researchers can take specific steps to ensure comprehensive data security:
- developing institutional policies: institutions should establish data security policies tailored to the specific needs and risks associated with research data. Policies should outline acceptable use, access controls, and protocols for data sharing;
- training and awareness programs: regular training for researchers and staff on data security best practices reduces human error and promotes responsible data handling;
- use of secure research platforms: institutions should adopt secure data management platforms and software that provide built-in security features like encryption and user permissions;
- periodic security audits: conducting regular audits of data security practices helps identify weaknesses and ensures that security measures remain effective and compliant with regulations;
- collaborating with IT and security experts: involving cybersecurity professionals in the research data lifecycle enhances security measures and provides researchers with technical expertise;
- data security in collaboration agreements: for projects involving external collaborators, institutions should establish data-sharing agreements that specify security expectations and data protection requirements;
- implementing data lifecycle management policies: institutions should develop policies that address data security at each stage of the data lifecycle, like categorizing data based on sensitivity levels, establishing procedures for the secure deletion or destruction of data and defining how long data should be retained in compliance with legal and institutional requirements;
- monitoring and incident response: effective data security policies include mechanisms for ongoing monitoring and incident management like implementation of systems to detect and alert on unusual activities or security breaches, and development of a clear plan outlining steps to take in the event of a security incident, including communication protocols and mitigation strategies.
Effective data security policies are adaptable and scalable, enabling researchers to protect data while accommodating the unique demands of different research projects.
As data security continues to gain prominence, regulatory compliance has become an essential aspect of research data management. Various data protection laws mandate secure data practices, and these regulations are constantly evolving. Researchers and institutions must stay informed about these regulations and adjust their security practices accordingly.
Regulatory compliance:
- General Data Protection Regulation (GDPR): GDPR applies to data collected from EU citizens, emphasizing strict data security, privacy rights, and penalties for non-compliance;
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA in the US mandates strict guidelines for handling health-related data, requiring healthcare researchers to implement specific security measures;
- Family Educational Rights and Privacy Act (FERPA): FERPA protects educational records in the US, relevant to research involving student data;
- National Data Protection Policies: many countries have established their own data protection laws, which research institutions must navigate when conducting international studies.
Future trends in research data security:
- integration of Artificial Intelligence (AI): AI can analyse vast amounts of data to identify unusual access patterns or potential security threats in real-time. Machine learning algorithms can automate responses to detected threats, such as isolating affected systems or alerting security personnel. AI can predict potential vulnerabilities by analysing past incidents and emerging threat patterns;
- blockchain for data integrity: blockchain provides a decentralized ledger where data transactions are securely recorded and cannot be altered retroactively. This facilitates secure and transparent data sharing among collaborators while maintaining data integrity;
- privacy-preserving computation: technologies such as differential privacy allow researchers to analyse sensitive data without compromising privacy;
- advanced encryption techniques: quantum encryption and homomorphic encryption could revolutionize data security, offering stronger protections against future cyber threats;
- zero trust security models: zero trust models operate on the principle that threats can come from both outside and inside the network. Users and devices must be authenticated and authorized before accessing resources, with continuous monitoring. It is also recommended to divide networks into small zones to maintain separate access to each part, reducing the potential impact of a breach;
- regulatory technology solutions: these are tools that help institutions automatically monitor compliance with various regulations by providing immediate insights into compliance status and potential issues as well as streamlining the creation, dissemination, and enforcement of data security policies.
The future of data security in research will be shaped by continuous advancements in technology and the evolving regulatory landscape. Institutions and researchers who adapt to these changes will be better equipped to protect data in an increasingly interconnected world.
Hajare R., Hodage R., Wangwad O., Mali Y., Bagwan F. (2021). Data security in cloud computing. International Journal of Scientific Research in Computer Science, Engineering and Information Technology, Vol. 8 (3), pp. 240–245.
Marquette University. (n.d.). Data Security for Data Management Plans. [online] [accessed 11/24/2024]. Available: https://www.marquette.edu/research-sponsored-programs/documents/data-management-planning-security-overview.pdf
Melbourne Polytecnhic Library. (n.d.). Research Data Management (RDM): Data Storage & Security. [online] [accessed 11/24/2024]. Available: https://libguides.melbournepolytechnic.edu.au/ResearchDataManagement/DataStorageandSecurity
Petkovič M., Jonker W. (2007). Security, Privacy, and Trust in Modern Data Management. Springer; 467 p.
Sun Y., Zhang J., Xiong Y., Zhu G. (2014). Data Security and privacy in cloud computing. International Journal of Distributed Sensor Networks, pp. 1–9. DOI: 10.1155/2014/190903
Velumadhava Rao R., Selvamani K. (2015). Data security challenges and its solutions in cloud computing. Procedia Computer Science, Vol. 48, pp. 204–209. DOI: 10.1016/j.procs.2015.04.171
Washington State University. (2024). Research Data Management: Data Security. [online] [accessed 11/24/2024]. Available: https://libguides.libraries.wsu.edu/rdmlibguide/datasecurity